Modi Government in Damage Control Mode As Apple Spyware Alert Revives Ghost of Pegasus
New Delhi: Late on Monday night, some two dozen individuals in India received alerts from Apple warning them that they are “being targeted by state-sponsored attackers who are trying to remotely compromise the iPhone associated” with their Apple ID.
Apple gave no specific details of which government or agency was doing the targeting, nor did it describe the nature of the remote compromise being effected. However, the general description it provided was graphic enough:
"These attackers are likely targeting you individually because of who you are or what you do. If your device is compromised by a state-sponsored attacker, they may be able to remotely access your sensitive data, communications, or even the camera and microphone. While it’s possible this is a false alarm, please take this warning seriously.”
For those previously targeted with the Israeli spyware Pegasus – I was among several journalists in India on whose phone the spyware was found – receiving Apple's alert (as I did) was a reminder of the state’s ingenuity in snooping on those it classifies as opponents. And of the ever evolving nature of spyware, malware and surveillance technology.
So, is this a warning that Pegasus is being used again? Or perhaps some other spyware like Predator? At this stage, we don’t know enough.
Spyware is big business globally and there are dozens of countries whose political, legal and ethical norms have created a permissive environment for ruling parties to weaponise surveillance for their own narrow partisan aims.
Is there a parallel with Pegasus?
In 2021, the Pegasus Project – of which The Wire was the India partner – used a leaked database of likely Pegasus victims to report on the targeting of thousands of individuals across dozens of countries by unidentified government clients of the Israeli spyware manufacturer NSO. Analysis of the numbers yielded geographical clusters and helped pinpoint the governments most likely involved.
In India, The Wire and its partners were able to identify more than 140 likely targets of Pegasus and were able to confirm the presence of the spyware on the phones of over a dozen individuals. Among these was the politician Prashant Kishor, whose phone yielded evidence of a compromise even as he was guiding the Trinamool Congress in its election battle with the Bharatiya Janata Party.
Given the nature and spread of the Indian targets on the leaked Pegasus database, it was evident that the targeting client was India.
Are the "state-sponsored attackers" this time also Indian?
In a statement/clarification emailed to reporters on Tuesday after several opposition leaders blamed the Modi government for targeting them, Apple said that it “does not attribute the threat notifications to any specific state-sponsored attacker.”
Since 2021, when it enabled the threat notification feature, Apple has sent similar alerts to persons in 150 countries around the world. What this means is that Apple has detected targeting attempts by multiple governments, at different points in time, and has sent out alerts to the affected individuals. In none of those cases has Apple identified the state-sponsor of the attack but it never really needed to. Thus, when two dozen journalists in El Salvador received warnings about state actors attempting to compromise their iPhones, it was clear as day that the targeting state was the government of El Salvador.
Government handlers have predictably clutched at the straw of understatement offered by Apple’s clarification to suggest there is some ambiguity about who might have targeted India’s opposition leaders. But as in the case of the Pegasus database of Indian numbers, it is only the Indian government which would have an interest in deploying spyware costing tens of millions of dollars against the range of targets that we have seen in India.
Why did Apple say some of its threat notifications may be ‘false alarms’?
The ‘false alarm’ suggestion has predictably been played up by a section of the media eager to bat for the Modi government without any reference to what Apple is actually trying to say.

NDTV breaking news flash
The words being quoted above is only a part of what Apple said in its statement and has actually been up on the company’s website for several months now. It notes that the sophisticated nature of the attacks make their detection difficult:
“State-sponsored attackers are very well-funded and sophisticated, and their attacks evolve over time. Detecting such attacks relies on threat intelligence signals that are often imperfect and incomplete. It’s possible that some Apple threat notifications may be false alarms, or that some attacks are not detected."
If anything, Apple is reinforcing the danger posed by state-sponsored attackers. Which is why the message it sent each of the victims on Monday night had this warning:
“While it’s possible this is a false alarm, please take this warning seriously.” (Emphasis added)
Did Apple help the Modi government’s attempts at damage control?
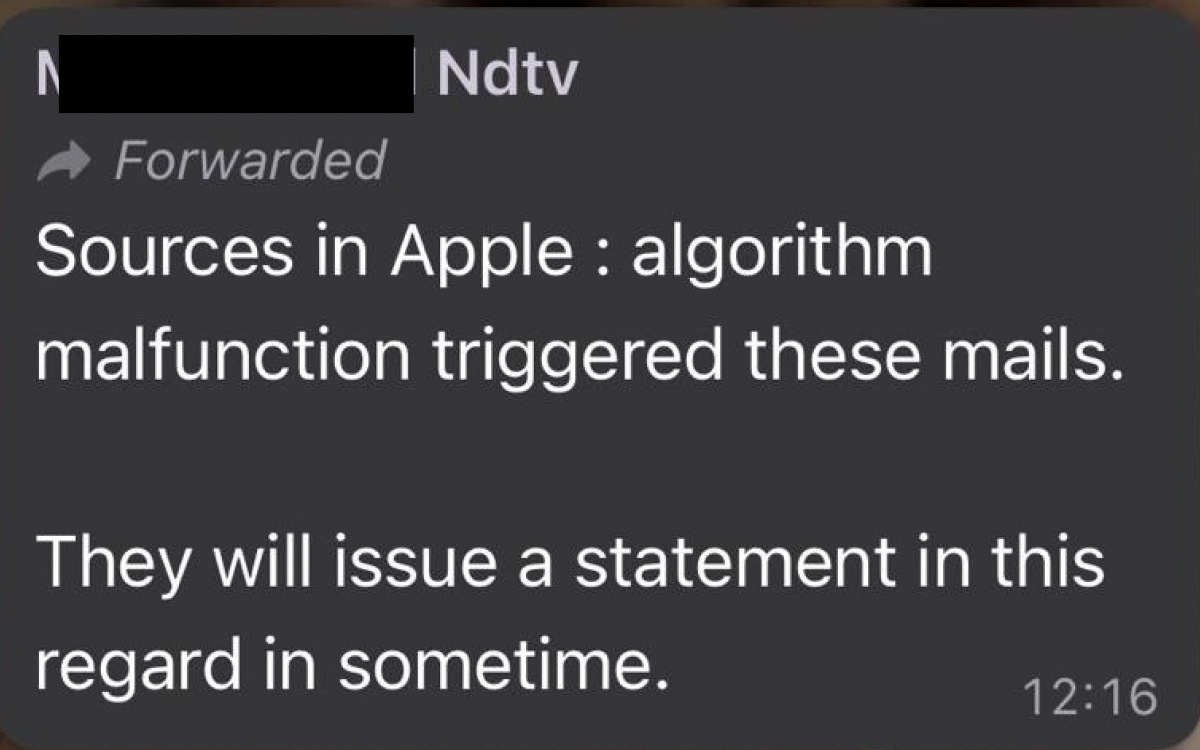
As opposition politicians took to Twitter one after the other on Tuesday morning to draw attention to the alerts they had received from Apple, the needle of suspicion clearly pointed towards the Modi government. The government’s first attempt at damage control was to float the suggestion via friendly journalists that these alerts had somehow been sent out in error. A number of television anchors started sharing a forward they had been sent claiming that ‘sources in Apple’ had said an “algorithm malfunction triggered these mails” and that the company “will issue a statement in this regard in sometime.”
Here is an example of one of these messages being shared at 12:16. Journalists with whom this was shared have said off the record that they received this ‘algorithm malfunction’ advisory from a senior government minister.
Around 1 pm, Apple’s India team indeed put out a ‘clarification’ and though it did not cite the (absurd) algorithm malfunction theory, it highlighted two pieces of information that the government was quick to latch on to.
Note that none of those who had received the alert the previous night and who had contacted Apple for more information and help in dealing with the threat received any response. But the company was quick to issue a statement which began with the declaration: “Apple does not attribute the threat notifications to any specific state-sponsored attacker.”
When The Wire contacted Apple India’s team to ask about the ‘algorithm malfunction’ theory, their reply was categorical: “This is untrue and we do not know where this came from… We’re advising all reporters the same on background.”
Before we analyse Apple’s ‘clarification' and its impact, the fact that a minister in government knew the company was going to “issue a statement in this regard in sometime” makes two things clear. First, that it was the Modi government which was keen for Apple to say something on the subject. And second, that there was likely some process of negotiation between the government and Apple about the contents of the ‘clarification’. Perhaps this is the reason why the Apple representative repeatedly told journalists to whom the ‘clarification’ was sent (including to The Wire) that, “It would be really helpful if you can note the 150 countries statistic in your story, found in the on background info below.”
The Apple statement’s reference to 150 countries was for the period since 2021 but the way IT minister Ashwini Vaishnaw recounted it, it was as if Apple had alerted people in 150 countries at the very same time as they had contacted those in India. This is what the minister told the media, as reported by ANI:
“Apple has released a clarification that the allegations by compulsive critics are not true. Such advisories have been sent to people in 150 countries. The people who cannot see the growth of the country are doing destructive politics…"
By creating the impression that the opposition politicians who had received the ‘state-sponsored attack’ alerts from Apple were part of a common group spread across 150 countries – all of whom had been informed at the same time – Vaishnaw was trying to shift the blame away from his government.
In reality, Apple launched its threat notifications process in November 2021, in response to reporting by the Pegasus Project. The first time Apple used the “150 countries” figure was in July 2022, when it became aware of a new vulnerability in the iPhone that was serious enough for it to introduce the ‘lockdown mode’ as a security feature and notify people around the world who might have been targeted through an iMessage exploit. As the Washington Post reported at the time:
“Researchers at the University of Toronto’s Citizen Lab captured what they said was a new version of Pegasus last year that exploited Apple devices through iMessage without needing any action from the victim to be installed. That triggered an Apple investigation and the notifications to targets.
“On a call with reporters Tuesday, Apple representatives said those warnings have now gone to residents of 150 countries, underscoring the dramatic scale of the problem.”
Are Apple’s warnings ‘vague’?
The IT minister has sought to make light of the emerging surveillance scandal by presenting Apple’s alert as “vague” because it lacks specifics. But this is not the first time Indian phone users have been alerted to the possible use of spyware against them. In 2018, WhatsApp wrote to two dozen people alerting them to the danger. In 2021, when The Wire analysed the leaked Pegasus database, it found the numbers of many of those whom WhatsApp had contacted.
Since spyware payloads are delivered through messaging vectors, it stands to reason that Apple, which has the ability to detect anomalies in the use of Apple IDs, iMessages and FaceTime calls, would be in the same position as WhatsApp was when it sounded the alarm five years ago.
What happens next?
While Apple may indeed have notified people across 150 countries over the past two years about hacking attempts on their phones, what it did on Monday night was to inform a group of opposition politicians and journalists in India whose vulnerability had presumably just come to light thanks to the activities of “state-sponsored attackers”. Which brings us back to the beginning: Who are these attackers?
Vaishnaw has said his government will probe these attacks and wants both Apple and the individuals it contacted to cooperate with it. Apple has said repeatedly that it is “unable to provide more information about what caused us to send … this notification, as that may help state-sponsored attackers adapt their behavior to evade detection in the future.” This means Apple, which probably knows a lot more than it has revealed, will not willingly come forward with more information. Nor is the Modi government likely to use whatever coercive powers it has in its arsenal to compel Apple to reveal what it knows because the information which emerges will likely damage it even further.
We are back to the same impasse last seen over Pegasus, where the government neither confirmed nor denied its use of the spyware and defied the Supreme Court’s direction that it cooperate with the probe panel that was set up under Justice (retd) Raveendran.
The Supreme Court allowed the Raveendran report to be shelved and chose not to begin contempt proceedings against the government. But the latest alerts from Apple provide confirmation that the use of spyware as a means of illegal surveillance is still continuing.
Using spyware against political opponents is not only a violation of an individual’s right to privacy but also amounts to subversion of the electoral process. The fact that public money is spent acquiring spyware which is deployed to further the interests of the ruling party also makes this an offence under the Prevention of Corruption Act and the Representation of People Act. In the United States, President Richard Nixon was forced to resign over a surveillance operation that looks like a tea party compared to the high-tech intrusive attacks being used against the opposition in India. But in India for some reason, none of this seems to matter.
This article went live on November first, two thousand twenty three, at zero minutes past six in the morning.The Wire is now on WhatsApp. Follow our channel for sharp analysis and opinions on the latest developments.




