Security Bug in MCA Portal Leaked Aadhaar-Based KYC Details of India’s Top Industrialists
India is rapidly digitising. There are good things and bad, speed-bumps on the way and caveats to be mindful of. The weekly column Terminal focuses on all that is connected and is not – on digital issues, policy, ideas and themes dominating the conversation in India and the world.
The Ministry of Corporate Affairs (MCA) portal, which is used by companies to file compliance activities under the Companies Act, has been reported to have many software glitches over the last year. The latest in the series of issues is of a security bug where Aadhaar-based KYC (know your customer) details of every company director, including industrialists and celebrities like Ratan Tata, Mukesh Ambani, Gautam Adani, Virat Kohli, and Shah Rukh Khan, were accessible without authorisation.
Security researcher Sai Krishna Kothapalli of Hackcrew published a report revealing details of the security issue. The report disclosed how the issue was fixed only after 11 months, after it was reported to the Indian Computer Emergency Response Team (CERT-In).

The information related to any company activity is made available to the general public for carrying out business transactions and verification, as part of market activities. The MCA portal performs an important function in this regard. It disseminates this information.
Under the Companies Act and Prevention of Money Laundering Act (PMLA), KYC norms exist to stop operations of shell companies involved in any illegal activities. A part of this KYC information is shared publicly to anyone who wants to verify details of the company or the director, with whom they are entering into a business contract under the Companies Act.
The security report details how the personal information that was available to be accessible on the MCA portal was much more than what is published by MCA. The data model shared in the report shows personal details, such as Aadhaar number, permanent account number (PAN), Voter ID, address, mobile number, and email ID. The data model includes internal flags designated by MCA, such as company director status, and whether director address is shared with another director to look for ghost directors and firms.

Redacted data model that has personal details of Ratan Tata.
This incident shows yet again how Aadhaar data that is being collected as part of the KYC process is often leaky because the institutions that collect it don’t safeguard this data. The institutions that are responsible for quality checks and security audits are Software Testing and Quality Certification (STQC) and Indian Computer Emergency Response Team (CERT-In). Both of them have continued to fail in responding to these issues. In the case of Aadhaar, its regulator Unique Identification Authority of India (UIDAI) has also consistently failed in regulating institutions that have leaked any Aadhaar data.
Also read: Indians’ Personal Data Breached Yet Again, but No Sign That Gaps Will Be Plugged
Ideally, CERT-In has to respond to all security vulnerabilities disclosed to them and immediately address them. Certain security vulnerabilities are hard to fix overnight and do require time to issue security patches to fix them. In this case, CERT-In was informed about the security issue in January 2023. While it flagged the issue, it did not fix it immediately. Even now, whether the issue is completely fixed is unknown, as CERT-In does not conduct any forensic analysis, potentially leading to the issue to continue to exist.
It took the security researcher 11 months, from January to December 2023, to analyse this process. The analysis also indicates a lack of capacity within CERT-IN to address such issues, even when they are reported to them.
Any security bug is a software bug that has been introduced because of poor software programming and quality control. Company secretaries and chartered accountants have been criticising the MCA portal over how the portal has several software issues and does not really work. However, a security issue, couple with all these other issues, does not come as a surprise. The lack of institutional accountability in this process continues to show how no one inside the government takes issues related to software seriously.
Because of the economic nature of this information, several companies and data providers collect this information and are already providing economic services on top of this information. There is an entire ecosystem of companies that provides business alerts and changes on company data as products to market actors, such as venture capitalists, investors, banks, news agencies, and other competitors. While there are companies which only provide information that is publicly being shared by the MCA, there are other entities which share the personal details of directors, such as their phone numbers and email IDs, as an extra service.
Some of these organisations or data brokers may have already obtained part or full information of these companies and directors through security bugs in the MCA portal. The MCA website only publishes basic information publicly when any user wants to verify the director identification number or their PAN. This is not excessive information and the Companies Act mandates this information to be public. The problem is with the additional information, such as Aadhaar, PAN, mobile numbers, and email ID, which is typically not provided.
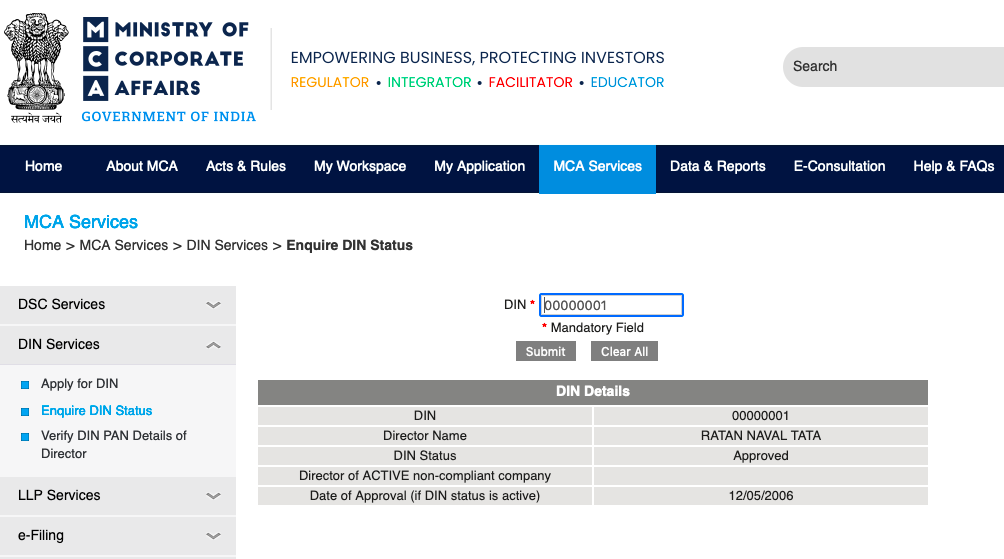
Ratan Tata’s director identification number on the MCA website.
Large organisations, such as government departments, collect information for a range of regulatory activities and are often legally required to do so. In this case, the ministry has to collect information for various compliance activities, but the problem is they are unable to control the flow of information, which is unacceptable. Policies like the National Data Sharing and Accessibility Policy mandate government departments to classify their datasets into open, shareable, and restricted categories to ensure the proper management of data flow. Unfortunately, this activity has largely been ignored by government departments.
Also read: Without a Data Privacy Law, India Must Consider Hazards of ‘Deanonymisation’ of Non-Personal Data
The Digital Personal Data Protection Act 2023, which is yet to be enforced, completely exempts government departments. Despite this exemption, in this case, the government still has to do a forensic analysis to identify the scale of the data leak.
The Ministry of Electronics and Information Technology has announced a draft national data governance policy, in which an India Data Management Office was supposed to classify various datasets with the government. However, this office has not been set up yet, and the process is still underway. Until this classification takes place, these issues will likely persist.
Interestingly, it was Ratan Tata who approached the Supreme Court demanding privacy regulation after his telephonic conversations were leaked as part of the 2G scam in 2010. Even after many years, the state is still figuring out how to enforce the fundamental right to privacy.
Srinivas Kodali is a researcher on digitisation and a hacktivist.
This article went live on January seventeenth, two thousand twenty four, at fifty-three minutes past three in the afternoon.The Wire is now on WhatsApp. Follow our channel for sharp analysis and opinions on the latest developments.




